Programmable Privacy 🔐
User privacy has long been an afterthought in the digital world—more of a joke than a guarantee. This blog explores how cryptography is shifting the balance, giving users back control over their data.
Remember the first time you whispered a secret to a friend? That moment when you shared something personal, knowing it would stay between just the two of you? There's a particular kind of freedom in that exchange—the ability to share without fear, to be vulnerable without consequence. For centuries, privacy has been the invisible thread weaving trust into our social fabric.
BUT, we stand at a fascinating crossroads. On one side, data breaches and privacy scandals have become so common that many of us suffer from "privacy fatigue"—that feeling of helplessness that makes you click "Accept All Cookies" without a second thought. On the other side, cryptographic innovations are finally reaching a level of usability that could fundamentally change this dynamic, shifting power back to individuals.
In 1993, a mathematician named Eric Hughes published "A Cypherpunk's Manifesto," declaring that "privacy is necessary for an open society in the electronic age." At the time, this was a radical idea. Most people still thought of the internet as a novelty, not something that would eventually know more about us than our closest friends and family.
Fast forward to today. Our digital footprints extend everywhere—from the websites we browse and the messages we send to the locations we visit and the purchases we make. In this data-saturated landscape, privacy isn't just nice to have—it's the foundation of trust in our digital relationships.
The Privacy Paradox
Have you ever noticed how we simultaneously value privacy while giving it away freely? We install password managers and fret over data breaches, yet willingly hand over our personal information to countless apps and services.
This "privacy paradox" exists because the current digital economy has made an implicit bargain with us: convenience in exchange for data. And the scales have tipped heavily toward convenience.
Consider these sobering statistics:
The average person has 80-90 online accounts
91% of consumers feel they've lost control of how companies collect and use their data
Data breaches exposed 4.1 billion records in the first half of 2022 alone
The traditional approach to privacy—trusting organizations to protect our data—is fundamentally broken. It's like handing your house keys to dozens of strangers and hoping none of them make copies.
This is where programmable cryptography enters the picture. Instead of depending on trust, what if we could mathematically guarantee privacy? What if your data could remain useful without being exposed?
From Encryption to Programmable Privacy: The Evolution
Traditional cryptography gave us the digital equivalent of locked boxes. I can encrypt a message so only the intended recipient can read it. This works well for point-to-point communication but falls short when we need to use our data across multiple services.
Think of it this way: traditional encryption is like having a safe deposit box at a bank. It's secure, but to use what's inside, you need to take it out—exposing it in the process.
Programmable cryptography changes this dynamic completely. It introduces sophisticated mathematical techniques that allow computations on encrypted data without ever decrypting it. This would be like allowing the bank to count your money without ever opening your safe deposit box.
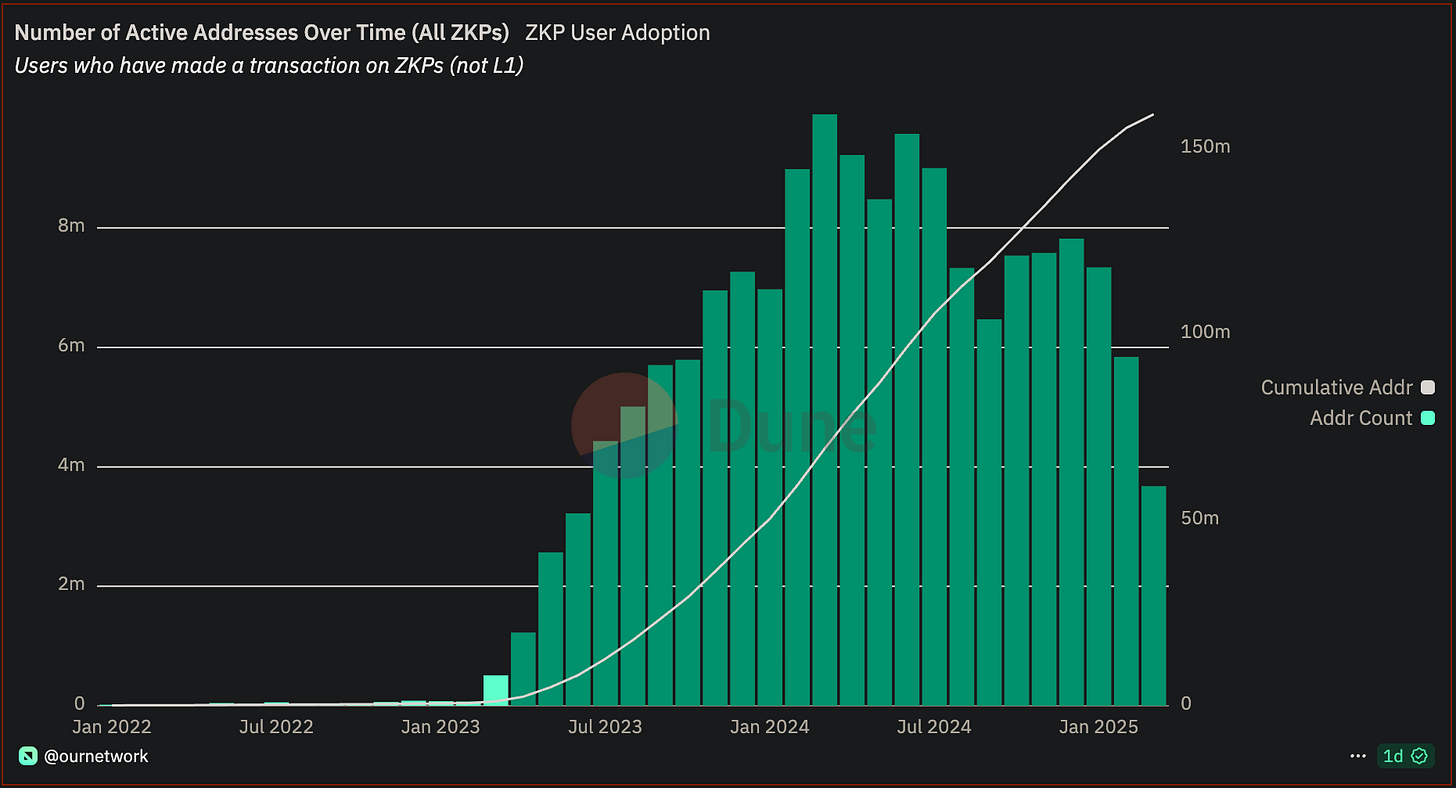
Zero-knowledge proofs (ZKPs) are a groundbreaking cryptographic technique that enables verification without revealing underlying data, making them essential for scalability and privacy in blockchain applications. Their adoption has been rapidly increasing, as shown in the chart below:
Key technologies enabling this shift include -
The revolution in programmable privacy is built upon a foundation of cryptographic primitives and techniques, each offering unique approaches to protecting sensitive information while preserving utility. These technologies represent the building blocks from which more complex privacy systems are constructed

Zero-knowledge proofs allow one party to prove they possess certain information without revealing the information itself. This mathematical breakthrough enables verification without exposure.
zk-SNARKs: Succinct Non-interactive Arguments of Knowledge power privacy on platforms like Zcash and Aztec, enabling transaction validation without revealing amounts or participants.
zk-STARKs: Scalable Transparent Arguments of Knowledge, used by StarkWare and ImmutableX, offer post-quantum security and remove the trusted setup requirement.
zkTLS (zk + TLS): A revolutionary extension of TLS protocol that allows authentication without revealing credentials, pioneered by Cloudflare and integrated into modern secure communication systems.
ZK Coprocessors: Specialized hardware from companies like Ingonyama and Axiom that dramatically accelerate proof generation, reducing times from minutes to seconds and making real-time zero-knowledge applications feasible.
MPC allows multiple entities to jointly compute functions over their inputs while keeping those inputs private from each other—enabling collaboration without compromise.
Homomorphic encryption permits computations on encrypted data without decryption, maintaining privacy throughout the processing lifecycle.
Fully Homomorphic Encryption (FHE): Implemented by Zama and IBM's FHE toolkit, enabling arbitrary computations on encrypted data.
Partially Homomorphic Encryption: Used by Evervault and Enveil for specific operations like addition or multiplication on encrypted values.
TFHE (Fast FHE): An optimization that makes homomorphic operations significantly faster, used by Fhenix.
TEEs provide isolated processing environments protected from the host system, creating secure enclaves for sensitive computations.
Intel SGX: Utilized by Secret Network and Phala Network to create protected memory regions that shield data from the operating system.
ARM TrustZone: Employed in mobile privacy solutions and embedded systems for secure processing.
AMD SEV: Leveraged by cloud providers for confidential computing offerings.
Who are building?
Private Transactions & DeFi (Aztec, Zcash, Aleph Zero, etc.)
Data Privacy & Ownership (Reclaim, Vana, Oasis, etc.)
AI & Computation Privacy (Primus Labs, Nillion, Fhenix, etc.)
zkCoprocessors & Infrastructure (Lagrange, Space and Time, Brevis)
zkTLS & Secure Bridging (Opacity, zkPass, Reclaim)
Let’s explore a few:
Private Transactions & DeFi
Aleph Zero is a high-performance, privacy-focused Layer 1 blockchain that integrates zk-SNARKs for private transactions and Secure Multi-Party Computation (sMPC) for confidential smart contracts. Using a DAG-based consensus, it ensures fast, scalable, and low-latency transactions.
Enigma - uses sMPC to enable private data processing in smart contracts. It’s designed for applications like secret auctions or confidential lending, where data stays hidden even during computation. Though less prominent lately, it’s a pioneer in this approach. It offers an alternative to ZKPs, broadening the privacy toolkit for DeFi developers.
Secret Network, built on Cosmos, Secret Network provides confidential smart contracts where inputs, outputs, and state are encrypted. It supports private DeFi apps like lending or DEXs (e.g., Secret Swap), with a focus on user control over data exposure. Cosmos integration enables cross-chain potential, appealing to privacy-first DeFi builders.
Data Privacy Solutions
Data privacy solutions are tools, technologies, and frameworks designed to protect personal or sensitive information from unauthorized access, use, or disclosure while enabling organizations to comply with regulations and maintain user trust. These solutions address the growing need to secure data in an era of widespread digitalization, where breaches and misuse are significant risks. They typically leverage cryptographic techniques, policy enforcement, and user-centric controls to balance functionality with privacy. Some examples-
Private AI Computation:
Nillion: Utilizes a novel technique called "Nil Message Compute" for distributed computation. These are called "blind computation," a form of secure multi-party computation (sMPC) that processes data without revealing it to the computing nodes. "Nil Message Compute" (NMC) refers to its proprietary approach, where data is split into fragments, computed on blindly by distributed parties, and reassembled only by the authorized user. It avoids traditional trusted intermediaries, aiming for trustless privacy. Nillion targets AI use cases like private model inference and data sharing, integrating with tools like Nada AI (an open-source framework for privacy-preserving AI).
Fhenix: Leverages FHE for training and inference on encrypted data. It is an Ethereum Layer 2 solution that uses FHE, a cryptographic method allowing computations on encrypted data without decryption. This enables private AI training and inference directly on-chain, where neither data nor model weights are exposed. Fhenix aims to make FHE practical by optimizing performance, targeting DeFi and AI workflows where confidentiality is critical.
Privacy-Enhanced Analytics:
Space and Time(SxT): Provides cryptographically-guaranteed SQL queries. It is a decentralized data warehouse that combines ZKPs with a SQL interface, allowing users to query data across blockchains and off-chain sources privately. Their Proof of SQL is a sub-second ZK coprocessor optimized for SQL and cryptographically verifies query results without exposing underlying data, targeting analytics for DeFi, gaming, and Web3.
Data Ownership & Monetization:
Vana: creates a user-owned data economy, where individuals store personal data in “data wallets”. Users can contribute data to AI training or analytics pools, earning rewards while controlling disclosure. Through its partnership with Phala Network, Vana integrates TEE solutions to enable secure data contribution, validation, and monetization within decentralized systems.
Oasis Network: Offers confidential smart contracts for data tokenization. Oasis uses TEEs to power confidential smart contracts on its blockchain, enabling data tokenization—converting data into tradable assets—while keeping it private. Its Sapphire EVM extends this to EVM-compatible chains, and recent features like ROFL support private AI and analytics.
Cross-Chain Privacy
Privacy-preserving infrastructure ensures that sensitive data remains confidential while enabling secure interactions across different blockchain networks. These solutions enhance cross-chain functionality while maintaining user anonymity and data protection.
Threshold Network: combines Proxy Re-Encryption (PRE) with Elliptic Curve Digital Signature Algorithm (ECDSA) to enable secure cross-chain transactions while preserving privacy. It ensures that encrypted data can be re-encrypted without exposing the raw data, allowing users to transfer assets or interact across multiple blockchains securely.
Axelar Network: provides interoperable privacy by enabling secure communication between blockchain ecosystems. It integrates ZKPs and encryption techniques to ensure that cross-chain transactions remain confidential while maintaining security and scalability.
Shade Protocol: builds privacy-preserving synthetic assets that can operate across different blockchain networks. By leveraging privacy-focused smart contracts and encryption techniques, it ensures that users can interact with DeFi applications without exposing their financial data. The protocol is designed to enable anonymous asset creation, trading, and lending across multiple ecosystems.
Each of these applications represents a different approach to solving the fundamental challenge of maintaining privacy while enabling valuable data use. As these technologies mature and combine, we're witnessing the emergence of comprehensive privacy stacks that protect data throughout its lifecycle - from collection through computation to sharing and deletion.
When I think about the most profound contributions of cryptography to society, I always come back to privacy. Not just privacy as a concept, but privacy as a right that technology can now programmatically enforce. This shift—from privacy depending on trust in institutions to privacy by mathematical guarantee—may be cryptography's greatest gift to humanity.


